Most of you know how to setup Microsoft Authenticator and most of you probably also know how to use it. Do you prefer the old-school implementation through the legacy portal or do you enforce it with conditional access rules. Did you know there is a third option?
In this blog post, I will guide you through the process of the third solution DUO multifactor authentication, and also why you should use this instead of Azure Multifactor authentication.
Why you should use DUO Multifactor
In most cases, companies prefer using DUO as a multifactor because of the easy adoption for end users. But did you know it can also help you make your environment more secure? In November 2018 Microsoft had a major outage on their Multi-factor services. A lot of companies were doomed and were not able to log on to the Microsoft 365 environment. Even administrators were not able to log in to disable the multifactor so company operations could work around the Microsoft outage. But there were some companies who were able to work. These companies had a Break glass protocol in place that made sure that in case of an emergency Administrators were always able to logon to the environment to disable the MFA services. But today end of the year 2022, almost Christmas, we all know that not using MFA could be deadly from a security perspective. And this is the part where DUO comes around.
DUO use case
With DUO multifactor it is possible to make sure break-glass accounts are also enforced with a Multifactor authentication without using Microsoft Multifactor. Since 2017 it is possible to use Custom controls within Conditional access. This basically means that you can create a grant control with something you want that needs to be applied before you grant someone access to your environment. But as Microsoft mentions custom controls have some limitations:
As Microsoft says:
Custom controls can't be used with Identity Protection's automation requiring Azure AD Multifactor Authentication, Azure AD self-service password reset (SSPR), satisfying multifactor authentication claim requirements, to elevate roles in Privileged Identity Manager (PIM), as part of Intune device enrollment, or when joining devices to Azure AD.
But we are not going to use Azure AD multi-factor for this purpose. We are going to use DUO to ensure our break-glass accounts are safe and will be enforced to have MFA.
Requirements
So what do we need to implement DUO Multifactor within our environment.
- A DUO free License (this is enough for our Breakglass implementation)
- A Microsoft 365 tenant with Azure AD P1 license
- Some knowledge about App registrations within Azure AD
Implementation
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications.
- Click Protect an Application and locate Microsoft Azure Active Directory in the applications list. Click Protect this Application. See Protecting Applications for more information about protecting applications in Duo and additional application options.
- Before you can proceed, Duo needs read access to your Azure Active Directory tenant. Click the Authorize button, which takes you to the Azure portal.
- Sign in with the designated Azure service administrator account that has the global administrator role for this Azure Active Directory. If required, complete Azure MFA for that service account admin user. Duo does not see or store your Azure Active Directory administrator credentials.
Once you've signed in to Azure, you must click Accept to grant Duo the read rights needed to access and read from your Azure Active Directory tenant. The permissions below are requested by DUO
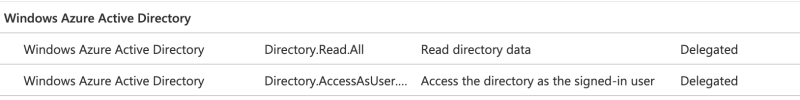
Accepting the Duo Azure Authentication application's permissions request redirects you back to the Microsoft Azure Active Directory application page in the Duo Admin Panel.Note the Custom control JSON text in the "Details" section of the page. You'll need to provide this information to Azure to complete Duo authentication setup.
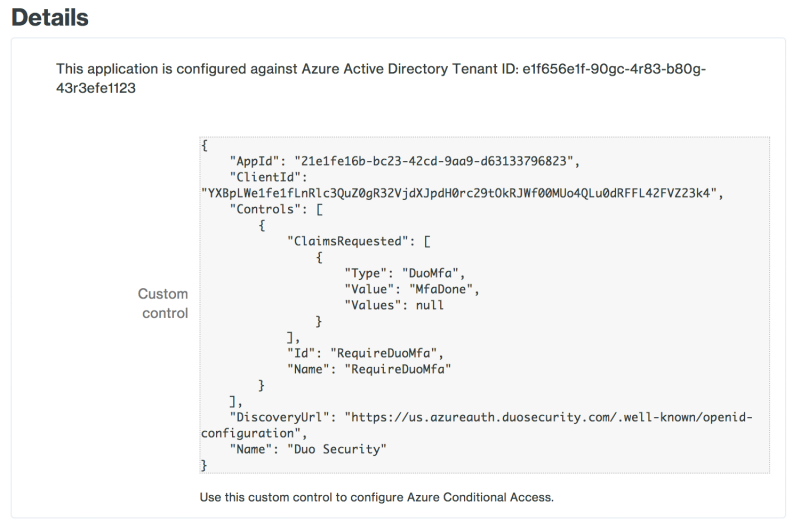
You can adjust additional settings for your new Azure Active Directory Duo application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy — or come back and change the application's policies and settings after you finish Azure setup (note that the "Hostname Whitelisting" settings have no effect on this application). If you do update any settings, click the Save Changes button when done.
Keep the Duo Admin Panel open so you can copy the custom control JSON text into the Azure portal in the next steps.
Implementation of the the custom control within Azure AD
- Log in to your Azure Active Directory tenant in the Microsoft Azure Portal as a global administrator (if you aren't already logged in).
- Go to Azure Active Directory → Security → Conditional Access.
- Click Custom Controls on the left, and then click New Custom Control.
- Remove the example custom controls JSON text and paste in the "Custom control" JSON text you copied from the Duo Admin Panel's Microsoft Azure Active Directory application page earlier.
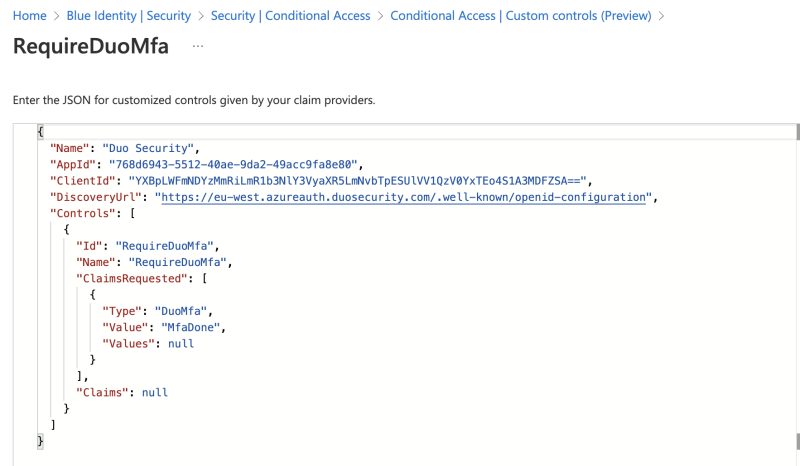
This will result in an extra option to select within the Grant menu of a conditional access rule.
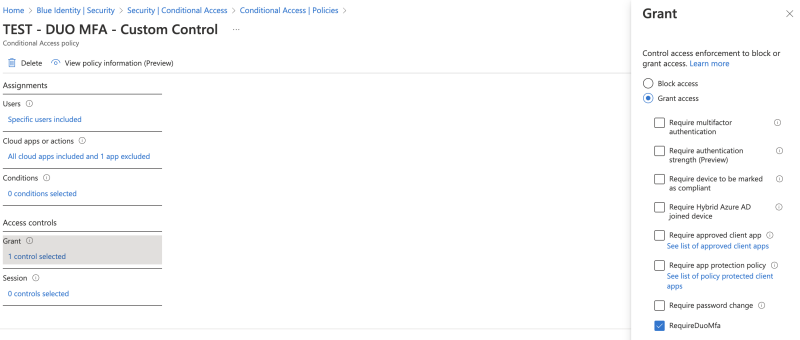
From this point on you can use Conditional access like you always did but with a extra option called "REQUIRE DUO MFA".
Break glass and DUO
In my example, i have created a security group with my Break glass account in there. The conditional access rule i created is targeted to all cloud applications except the Microsoft Azure Management Portal. But if you want to make sure the security of your break glass account is arranged properly you have to switch these around. This means only adding the Microsoft Azure Management Portal to the conditional access rule and excluding all other apps. In this way, your Break glass account is always able to logon to the tenant within using MFA from Microsoft Azure but with the use of DUO MFA instead.
Note: make sure you always test Conditional access rules before implementing them to prevent being locked out of your environment. Also, make sure the password length of your break glass account is more then 15 characters long which almost makes MFA obsolete




